The 2011 PlayStation Network Hack – What Actually Happened?
On April 4th, 2011, the Hacktivist group Anonymous brought down Sony’s PlayStation Network (PSN) with a Targeted Distributed-Denial-of-Service attack. (DDoS) Anonymous had warned Sony of retaliation after Sony took legal action against two people. George Hotz, known as GeoHot, and Alexander Igorrenknov, known as Graf_Chokolo. Anonymous’ statement to Sony was clear and right to the point. “Congratulations, Sony. You’ve now received the undivided attention of Anonymous. Your recent legal action against our fellow hackers, GeoHot and Graf_Chokolo, has not only alarmed us but has also been deemed wholly unforgivable. You have now abused the judicial system in an attempt to censor information on how your products work. You have victimized your own customers merely for possessing and sharing information and continue to target every person who seeks this information. In doing so you have violated the privacy of thousands. This is the information they were willing to teach to the world for free. The very same information you wish to suppress for sake of corporate greed and complete control of the users. Now you will experience the wrath of Anonymous. — You must face the consequences of your actions, Anonymous style. Knowledge is Free. We are Anonymous. We are legion. We do not forgive. We do not forget. Expect us.”
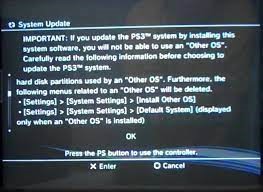
In 2009 GeoHot had announced on his blog that he was interested in hacking the PlayStation 3. His method in doing so was to utilize Other OS. Which gives users the ability to run Linux. Sony was no stranger to allowing its users to run Linux on their hardware. It was also available on the PlayStation 2. But was optional. This required a hard drive, mouse, keyboard, and a Linux installation disk. Other OS on the PlayStation 3 in contrast was presented as a feature. GeoHot published his findings on his page and found a method to bypass the security hypervisor. His findings caught the attention of Sony. Who in March of 2010, released an update for the PlayStation 3 that completely removed Other OS and suppressed anyone who wanted to continue GeoHot’s previous work. In July of 2010, GeoHot announced that he was retiring from the PS3’s hacking scene. “It was a cool ride, and I learned a lot. Maybe I’ll do in the next few years, a formal goodbye.” GeoHot stated. But Sony couldn’t breathe a sigh of relief for much longer. Later that year, FailOverflow, a hardware hacking group motivated by the removal of Other OS found a way to obtain the private key for the PlayStation 3. Without having to make any hardware modifications to the console. At that point, the key itself wasn’t enough to execute unsigned code, but it could be used to run software that could. GeoHot who had previously stepped away from the PlayStation community had combined his findings with FailOverflow’s discovery and created a package to run unsigned code on the PlayStation 3’s hardware.
In early 2011, GeoHot posted his method. Along with his files onto his website. Around the same time, Graf_Chokolo had released a custom firmware that would reinstate Other OS onto the PS3 that would allow previous owners to run Linux once again. In January of 2011, Sony filed a court order against GeoHot and FailOverflow under violation of DMCA and Computer Fraud. Later, Graf_Chokolo’s house was raided by law enforcement. He was placed under arrest facing numerous charges. Hacktivist group Anonymous responded to Sony later that year. Which was a direct response to the court orders and arrests made. Anonymous made cyberattacks against Sony’s servers for three days. The disruption was known as “#opSony”. Operation Sony’s objective was to do whatever it could to undermine Sony’s operations. On April 7th, Anonymous halted its attack. Anonymous realized that it was harming the consumers rather than Sony. So, they decided to stand down. “Anonymous is not attacking the PSN at this time.” Stated the group. “We have realized that targeting the PSN is not a good idea. We have therefore temporarily suspended our action until a method is found that will not severely impact Sony customers. Anonymous is on your side, standing up for your rights.” Normal PSN service resumed after that. But on the morning of April 19th, PSN was down again. But Anonymous wasn’t responsible for the shutdown. It was Sony. Two days later, Sony took the PSN servers offline again. “As you are no doubt aware, the current emergency outages continuing this afternoon and all Sony Online Network Services remain unavailable.” Sony had warned its consumers that it could be a full day or more of downtime. The very next day, Sony had announced in a press release that there was an “external intrusion” on their system that affected both PlayStation Network users and Curiosity Services and admitted that they had disabled PSN on April 20th. PSN remained offline for another week. Which caused outrage from customers who were not sure of what was happening. But Sony emerged, announcing what was to be a massive security breach that affected 77 million users. “Although we are still investigating the details of this incident, we believe that an unauthorized person obtained the following information that’s provided. Name, address, country, email address, birthdate, PlayStation Network password and login, and PSN Online ID. It’s also possible that your profile data, including your purchase history and billing address and your PlayStation Network Curiosity password security answers, may have also been obtained.” Said the corporate giant. The PlayStation Network had remained offline. Sony brought in a security firm to investigate the breach. As well as perform updates to the service.
On April 1st, 2011, Sony had completed the upgrade of its security on PSN servers and held a press conference in Japan to outline what it was doing to protect its customers. Sony executives apologized and offered their consumers a welcome back package. Which consisted of two free games, and 30 days of free PlayStation Plus. As well as a free year of identity theft protection. On May 2nd just one day after, Sony executives apologized once more. Sony Online Entertainment had been breached by hackers. Stealing more than 24 million users’ information. “We are today advising you that the personal information you have provided us in connection with your S.O.E. account may have been stolen in a cyberattack.” Sony Online Entertainment was not directly linked with the PlayStation Network. Rather, its division was responsible for multi-player online games. Sony Online Entertainment had services because of this breach. In June of 2011, hackers had also taken down yet another Sony network. This time, Sony Pictures. Hacking group LulzSec took responsibility. “Every bit of data we took was not encrypted. Sony had stored one million passwords that of its customers in plain text. Which means it’s just a matter of time taking it.” Sony had denied the claims. But later LulzSec uploaded a 5MB file outlining how the hack was performed via very simple single sequel injection methods.
In September of 2011, the FBI had announced that they have made arrests in the Sony Pictures attack. Two members of LulzSec were arrested and charged. Several news outlets claimed that law enforcement had made arrests in the Sony hack. Which many had wrongfully assumed that it was for the PlayStation Network. Many people are unsure of the cause of the PlayStation Network hack. One popular theory at the time was that there were potential discussions about a custom firmware known as Rebug that could’ve been responsible. Rebug is in fact, a custom firmware for jailbroken PS3s which enables Homebrew and piracy on those systems. There was also the ability to rename all functionality that should only be available to debugged versions of the PlayStation 3. Including access to the Internal Developer Network. Which is used to test online functionality during a game’s development. This is very similar to the XBOX 360’s PartnerNet system. The Developer Network simulates a user purchasing a game through a placeholder credit card. This meant that hackers could steal and download the pre-release beta, as well as pre-released titles. But this exploit was later patched as part of the PSN downtime. But it was not responsible for the hack itself. At the time, Sony had accused Anonymous. Claiming that they have found files on their server “Anonymous” and “We Are Legion”. But as of the publishment of this article, no arrests have been made or recently reported.

My name is Diamond. I just graduated high school and now I'm producing content part-time online. My most popular profile is @BlindOS_22 on TikTok which...














Diamond M. Garcia • Feb 18, 2023 at 1:44 pm
Want to read more? I’m publishing stories on my site: blindos.online